Loading blog post...
Why Smart Contract Audits Keep Failing And How to Fix the Problem for Good
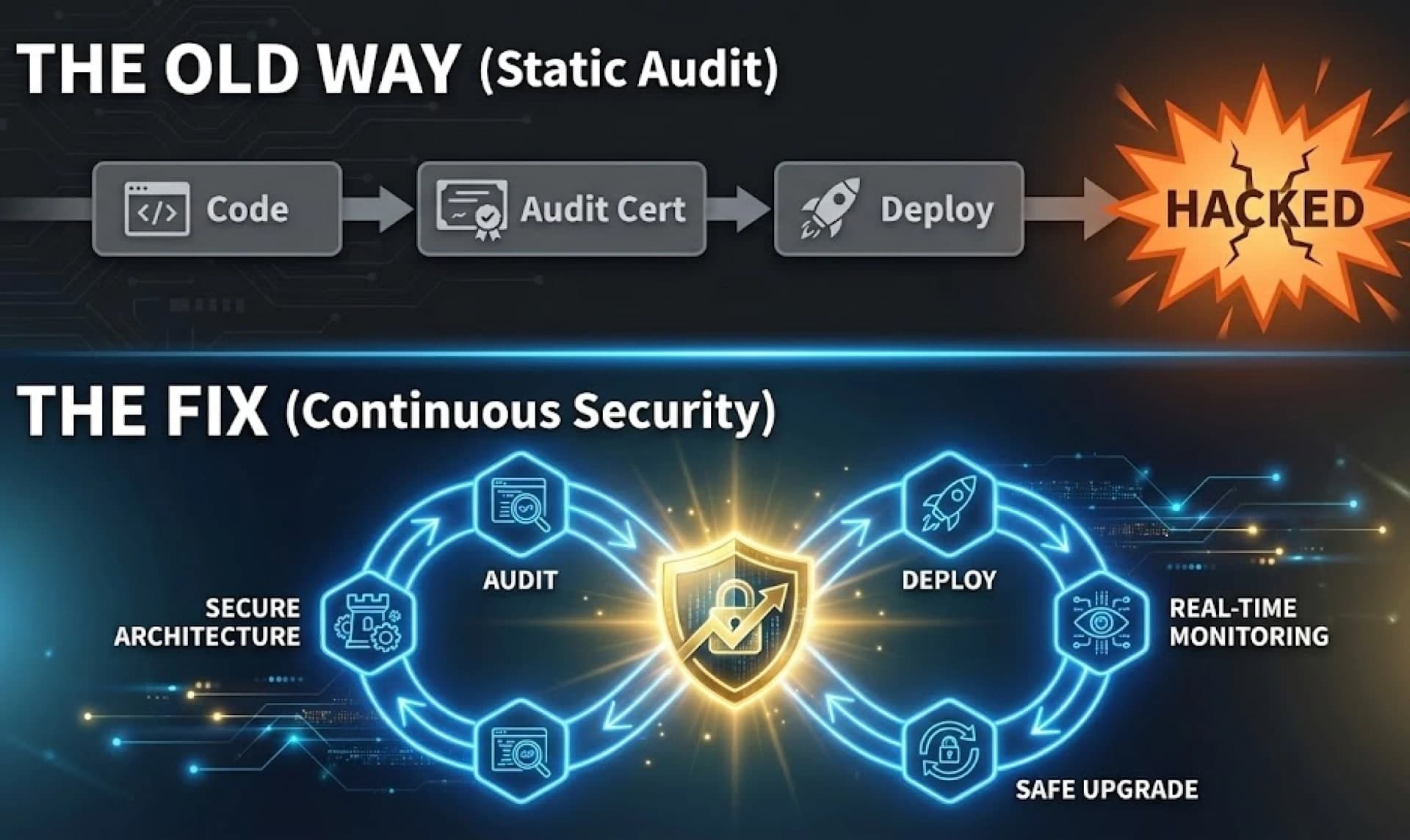
Smart contract audits aren’t failing because auditors are incompetent. They fail because teams treat audits as certificates instead of continuous security processes. This guide exposes the real blind spots behind audited exploits and explains how to fix smart contract security for good.
The Web3 ecosystem always promised unstoppable code, self-sovereign systems and permission-less innovation. But in 2025, the reality looks very different: protocols get exploited within hours of deployment, “audited” projects still lose millions, and the phrase “we passed an audit” has become more of a meme than a milestone.
The truth is harsh but unavoidable, smart contract audits are failing, not because auditors are bad, but because the ecosystem misunderstands what an audit actually is. ****Teams treat them like certificates. Investors treat them like insurance. Users treat them like guarantees. Meanwhile, attackers treat them like background noise.
Smart contract auditing is not broken. The approach to auditing is broken.
This guide goes deeper than generic advice. It breaks down the root cause behind failing audits, exposes the blind spots that no one talks about, and lays out how to fix the problem in a way that actually protects a protocol, not just its reputation.
Why Smart Contract Audit Quality Breaks Before the Review Even Starts
A smart contract audit begins when the team hands over their architecture, documentation, threat models, upgrade plans, dependency maps, oracle assumptions, and cross-chain interactions. Most teams skip every single one of these steps. They drop reviewers into a codebase without explaining the larger ecosystem surrounding it.
This is the silent killer of audit quality.
Code without context forces auditors to guess what “intended behavior” means. When intention is unclear, issues get misclassified, logic flows get misunderstood, and risks slip through because reviewers don’t know the full economic environment the contract will operate in.
This issue is also why so many early-stage teams gravitate toward cheaper reviews. They assume a low smart contract audit cost is just “affordable security,” not realizing that low price often signals zero architectural review, minimal adversarial modeling, or outsourced junior-level staff. A rushed audit may technically “complete,” but it leaves the protocol far more vulnerable than the team realizes.
Bad preparation doesn’t just weaken the audit, it ensures its failure.
The Blind Spots: Why Smart Contracts Audit Reports Miss Real Attack Vectors
Most exploits don’t occur in the lines of code auditors read, they occur in the lines of code they never saw.
A typical smart contracts audit focuses on the Solidity files inside the repository. But real-world exploits target the layers around those files - relayers, routers, keepers, backend scripts, admin keys, UI signing flows, oracle updates, and integration assumptions.
Attackers don’t care about boundaries defined by an audit document.
They attack everything you rely on.
This is why teams often announce confidently “we passed an audit” shortly before losing their treasury. The audit didn’t fail. The scope failed. The documentation failed. The assumptions failed. The supporting infrastructure failed.
Even the best smart contract audit companies cannot audit what they were never shown.
This systemic blind spot is exactly why protocols with “perfect reports” still get exploited days later.

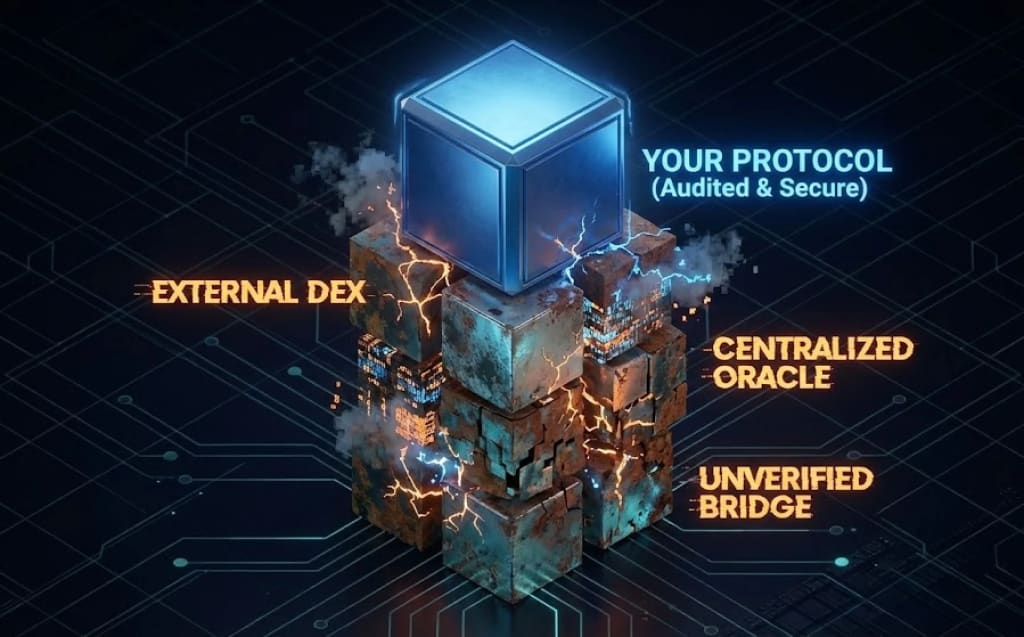
The Composability Problem: Why Auditing Smart Contracts Isn’t Enough in 2025
Modern dApps are not isolated systems. They rely on price feeds, routers, middleware, bridges, meta-transactions, relayers, backend signers, and frontends that communicate with dozens of external systems. A smart contract audit firm can confirm your code behaves correctly but it cannot guarantee anything about the protocols you depend on.
Composability is both Web3’s superpower and its greatest weakness. If one dependency cracks, your protocol inherits that flaw instantly. Auditing smart contracts made sense in 2019. In 2025, you’re auditing an ecosystem, not a file.
This is why “we passed our audit” is a meaningless statement by itself.
Soft Targets: How NFT Smart Contract Auditing Became the Most Overlooked Risk Zone
NFT projects often assume they aren’t high-risk because they don’t custody large treasuries. That assumption has cost creators millions. NFT smart contract auditing frequently overlooks metadata sources, forced mint bypasses, signature drainers, privileged mint logic, trait manipulation, and marketplace execution quirks.
NFT contracts look simple but behave unpredictably under composable conditions. Attackers know this and they target them precisely because security is treated casually. An NFT audit may pass, but the real vulnerabilities exist in the interactions, not the mint function itself.
Most NFT exploits don’t come from mint functions, they come from how those functions integrate with the broader ecosystem.
The problem isn’t NFT contracts being inherently weak. The problem is treating NFT audits as trivial.
Auditing Smart Contracts Doesn’t Cover Upgrade Behavior
Most exploits don’t occur at deployment. They occur after.
A protocol can pass an audit, ship safely, and then six months later introduce a tiny upgrade that bypasses every safety check the audit validated. This is why so many protocols look secure “on paper” but still collapse after governance changes, liquidity adjustments, or logic migrations.
Smart contract auditing doesn’t automatically account for future upgrades. Teams must enforce the discipline themselves.
That discipline rarely exists and attackers capitalize on it immediately.
How to Fix the Smart Contract Audit Problem for Good
Fixing audits isn’t about finding better auditors but about redesigning the way teams approach security.
The only sustainable solution is to shift from audit-first thinking to architecture-first thinking. Security must begin long before the audit, survive long after deployment, and evolve continuously through every upgrade.
True protection comes from a culture where every decision - architecture, code, deployment, governance, integrations, oracles is evaluated through an adversarial lens.
Audits also fail when they stop after deployment. Every upgrade, migration, governance vote, liquidity expansion, and new integration requires the same level of scrutiny as a pre-launch audit. Security is not a milestone. It’s a continuous loop.
A smart contract audit firm can find vulnerabilities, but only a security-driven development culture can prevent them from reappearing.
When teams approach smart contract auditing as a constant practice not a one-time purchase, the entire system becomes safer, stronger and harder for attackers to exploit. If that’s the standard you want to build by, reach out to EthElite today.
FAQ: Smart Contract Audits in 2025
Q: Are smart contract audits actually reliable?
A: Yes, when used correctly. Audits fail not because auditors miss everything, but because teams treat them as guarantees instead of inputs. An audit is only as reliable as the architecture, documentation, and scope the team provides.
Q: Why do exploited protocols still have “perfect audit reports”?
A: Because the exploit usually lives outside the audited files, in upgrade logic, integrations, admin permissions, or off-chain systems the auditors were never shown. Attackers strike where the audit scope ends.
Q: Does a higher smart contract audit cost mean better security?
A: Not necessarily. High prices don’t replace weak preparation, incomplete documentation, poor architecture, or unmodeled dependencies. Expensive audits still fail if the team hides complexity or can’t explain intended behavior.
Q: What’s the biggest blind spot in auditing smart contracts today?
A: Composability. Protocols rely on a dozen external systems - routers, price feeds, keepers, relayers, cross-chain bridges — and most audits review only the repo, not the ecosystem. That’s why attackers target connections, not code.
Q: Are NFT smart contracts safer because they don’t manage liquidity?
A: No. NFT exploits come from metadata manipulation, trait switching, signature abuse, marketplace quirks, and forced mint bypasses. The risk is different, not lower.
Q: Why do teams fail audits after passing one already?
A: Because the exploit usually appears after a governance vote, a small upgrade, a liquidity parameter change, or a new integration. The old audit doesn’t protect the new behavior.
Q: How often should a project audit their smart contracts?
A: Every time you:
- upgrade logic
- integrate a new system
- modify governance permissions
- adjust oracle or pricing dependencies
- push major liquidity changes
Auditing is continuous, not calendar-based.
Q: What’s the right way to fix the audit problem?
A: Shift from “audit-first” to architecture-first and continuous security. A smart contract audit company can find bugs, but only a security-driven engineering culture prevents them from returning.
The Reality: Smart Contract Audits Don’t Fail, Inefficient Teams Do
When the architecture is threat-modeled, when the audit is continuous, when integrations are scrutinized, when upgrades are unsafe by default, when assumptions are documented, when admin controls are constrained, and when monitoring is real-time, attackers lose their edge.
A smart contract audit is not a certificate. It is a weapon if you know how to use it.
Share with your community!