Loading blog post...
The Complete Guide to Bulletproof dApp Security in 2025
In 2025, dApp security is no longer about fixing bugs after deployment—it’s about surviving in an adversarial, automated attack environment. Modern exploits target logic flaws, upgrade paths, infrastructure layers, and predictable execution flows. This guide breaks down how attackers think, where real vulnerabilities live, and how to build dApps with security embedded from architecture to post-deploy monitoring.
Let’s be honest, Web3 isn’t the peaceful decentralized utopia we wanted. It’s a battleground.
In 2025, blockchain security isn’t just an engineering concern, it’s the difference between a protocol thriving or disappearing overnight. We’ve reached a point where attackers write scripts before founders write whitepapers, and if you’re building a dApp, you’re already being targeted even if you don’t know it yet.
The goal of this guide?
To walk you through the real security landscape with actionable insights for who want to build without fear.
The New Age of dApp Vulnerabilities: What Hackers Actually Look For
Picture a hacker scrolling through your contracts like a buffet menu. They’re not looking for rare bugs, they’re hunting the predictable, the lazy, the “I’ll fix it later” issues.
Here’s what’s trending on the exploit list in 2025:
Logic Bombs Hidden in Edge Cases:
Attackers love spots where “this will never happen” logic lives. Unexpected token decimals, weird fallback behaviors, malformed calldata - they’re all goldmines.
Broken Upgrade Paths:
Proxy contracts are everywhere now, and you’d be shocked how many teams leave the upgrade admin wallet unsecured. One compromised signer, and the attacker can deploy a malicious implementation.
Event Spoofing Manipulation:
Some devs rely on emitted events for critical off-chain processes. Hackers know this. Events can lie, and if your backend trusts them - boom.
Poorly Designed State Machines:
Complex protocols like lending markets or perpetuals rely on tight state transitions. One transition out of order? Instant chaos.
Bottom line:
Modern dApp vulnerabilities are rarely obvious, they thrive in the logic layer where devs get overconfident.

Web3 Security in 2025: The Attack Surface No One Talks About
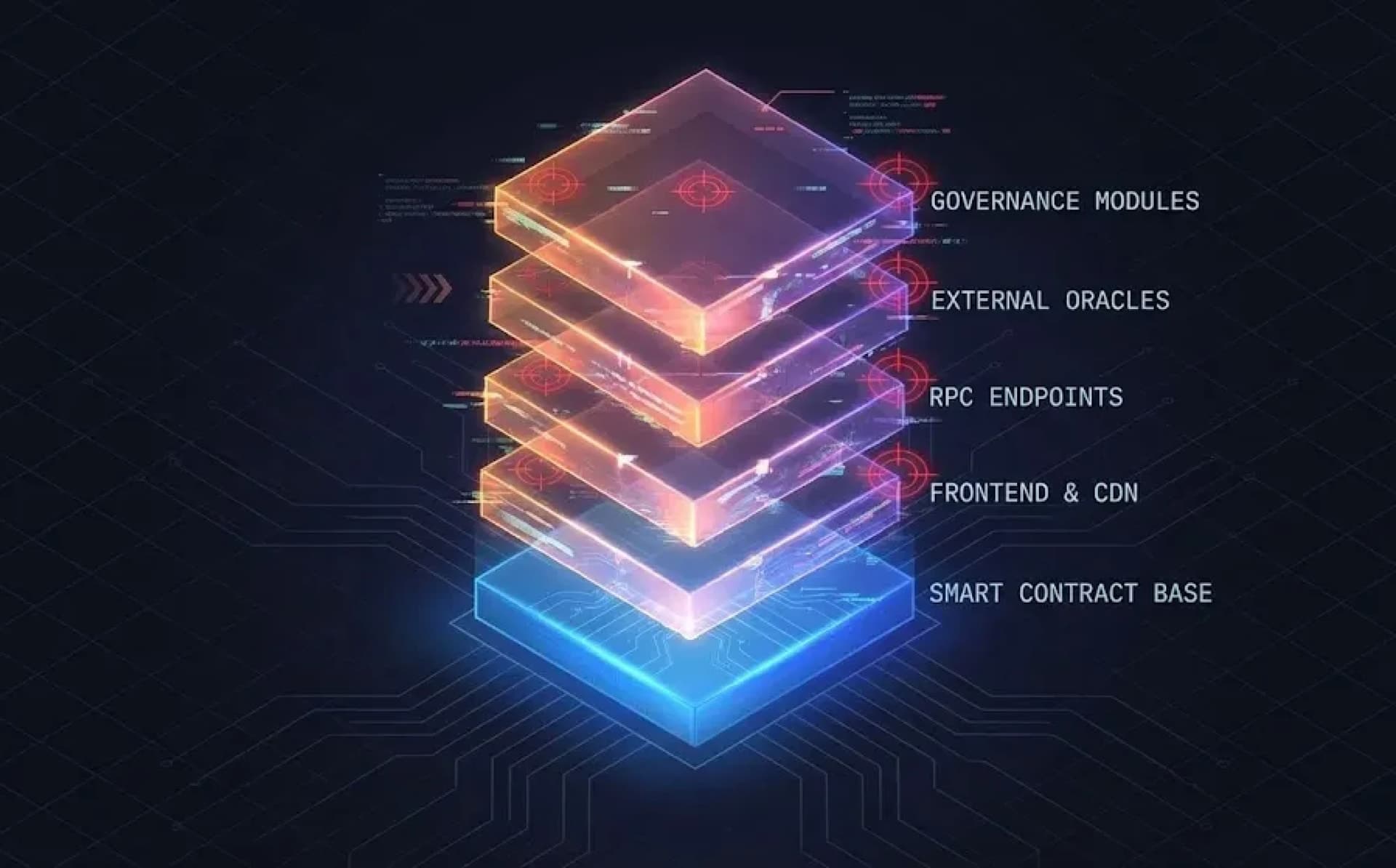
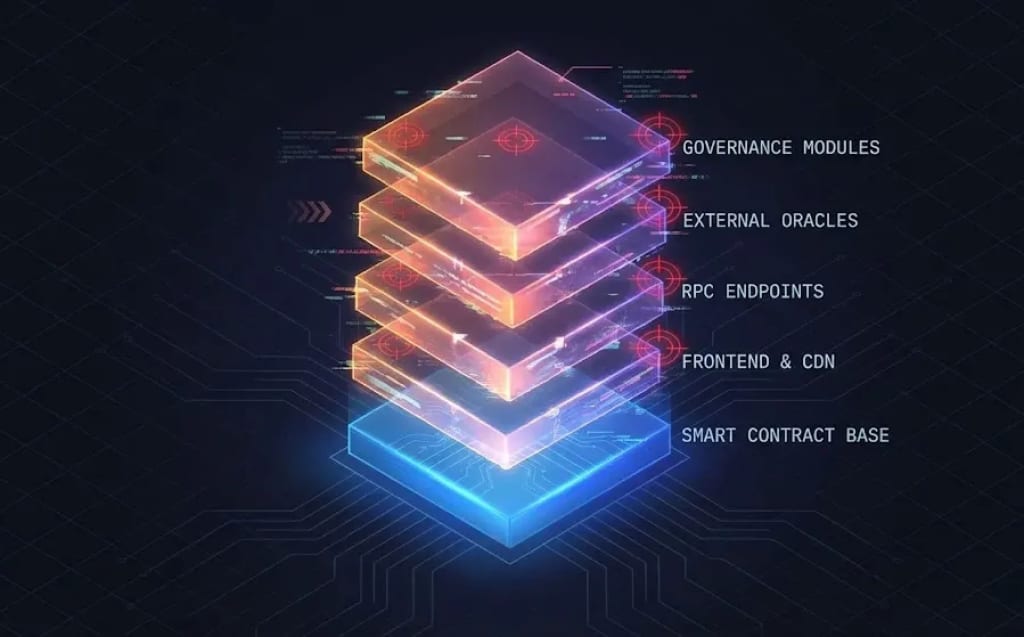
Web3 security is a full-stack responsibility. A decentralized application doesn’t end at its smart contracts. It extends to RPC providers, indexers, frontend hosting, wallet integrations, backend automation, and cross-chain components. Any weak link becomes an entry point.
Compromised RPC endpoints can manipulate gas parameters or censor transactions. A hijacked frontend CDN can feed users malicious transaction payloads. Bridge integrations can inherit vulnerabilities from external ecosystems. Even governance modules are attack surfaces, as vote accumulation strategies can lead to silent takeovers.
Security is no longer about auditing one repo. It’s about securing every component that influences user transactions.
For a deeper breakdown, see how our team does secure smart contract audits.
Inside the Mind of a dApp Hacker
Understanding attacker behavior is crucial. dApp hacking is an industry with its own economics, tooling and workflows.
The Incentive Model:
Attackers evaluate upside vs. effort vs. consequences. A protocol with high TVL and weak monitoring becomes an obvious target. If the payout exceeds the required skill and the likelihood of attribution is low, the attack becomes viable.
The Flash Loan Effect:
Flash loans have eliminated capital requirements. Anyone can borrow millions, execute a sophisticated exploit, and repay the loan in a single transaction. This enables attacks that were previously impossible due to capital constraints.
MEV Exploitation:
The MEV ecosystem isn’t always malicious, but it regularly extracts value at users’ expense. Front-running, back-running, and sandwiching are automated processes that exploit predictable transaction flows. MEV extraction has grown into a multimillion-dollar industry, and dApps with predictable execution patterns become prime targets.
Security Markets:
A vulnerability discovered in your contract may pay $75,000 in a bug bounty or $3 million on a black market. Hackers perform the same calculation developers do, but with different incentives. When your bounty program is cheaper than exploiting you, you lose talent to criminal markets.
Delayed Attacks:
Professional attackers don’t rush. They identify issues, monitor your TVL, and wait until you’re holding enough assets to justify action. This is why a past audit cannot guarantee present safety.
For teams preparing for a formal assessment, can checkout our smart contract audit services for Web3 applications.
What a Secure dApp Deployment Looks Like in 2025
A secure deployment is defined by its process of execution. A well-designed protocol maintains consistent behavior under stress, avoids ambiguous user interactions and restricts administrative control to predictable, multi-party mechanisms. Critical functions have time delays rather than instantaneous execution. External integrations are validated. Oracles incorporate sanity checks, fallback sources, and circuit breakers. Monitoring systems detect abnormalities within seconds, not hours.
Security isn’t determined by an audit report. It’s determined by how well the system handles the unexpected.
Your Secure dApp Development Guide: Building Defense From Day One
You can’t secure a dApp after it’s built. Security has to be in the DNA from the first commit.
Let’s lay down the blueprint:
1. Design With Attackers in Mind
Before writing your first line of Solidity, define:
- assumptions
- trust boundaries
- maximum blast radius
- fallbacks if something breaks
Most hacks happen because devs assume happy paths.
2. Follow Immutable-First Architecture
Code only what must be upgradeable.
Everything else should be frozen and predictable.
3. Threat Modeling Sessions Every Sprint
Your engineering spec should include:
- potential exploits
- attacker motivations
- worst-case scenarios
- mitigation layers
This transforms teams from reactive to proactive.
4. Comprehensive Testing Beyond Unit Coverage
Don't stop at “90% test coverage.”
Test:
- sandwiching
- MEV scenarios
- oracle failures
- reorgs
- gas griefing
- denied service edge cases
Now you’re really building secure dApps.
- Deploying With Confidence: Your Final Checklist for Bulletproof Security
If your dApp passes this checklist, you’re in the top 1% of secure dApp developments in 2025:
- full automated scanning + manual audit
- transaction simulator added to frontend
- upgrade keys secured or transferred to multisig
- emergency pause + throttling mechanisms
- oracle sanity checks
- rate limits for sensitive actions
- unit + integration + adversarial testing
- post-deploy monitoring bots
- documented threat model
- public bug bounty live day one
You’re no longer hoping your protocol survives, you’re ensuring it.

FAQ: dApp Security in 2025
Q: Why are dApps getting hacked more frequently now?
A: Because attack surfaces have expanded far beyond smart contracts. Everything from RPC endpoints to CDNs to governance modules can become an entry point. Attackers also have better tooling, automation, and incentives than ever before.
Q: Is a smart contract audit enough to secure my dApp?
A: No. An audit is a snapshot in time, not a permanent shield. Architecture, monitoring, automated safeguards, and continuous evaluation matter just as much as the audit itself.
Q: How do I know if my protocol is a target?
A: f your dApp touches money, governance, or user data, you’re a target. Attackers don’t wait for TVL to grow; they watch repos, commits, and contract deployments in real time.
Q: Where do most vulnerabilities actually come from?
A: Poor assumptions, insecure upgrade paths, flawed state machines, under-tested edge cases, and integrations with external systems that weren’t built securely. Logic vulnerabilities, not classic bugs cause most major hacks.
Q: What’s the best way to prepare for an audit?
A: Finish internal testing, document assumptions, freeze scope, and review upgradeability paths. For teams preparing for a formal assessment, you can check out our smart contract audit services for Web3 applications.
Q: How often should my dApp be audited?
A: Every time you push meaningful changes, integrate external protocols, modify economic parameters, or upgrade core logic. Security is continuous, not scheduled.
Ready to Level Up Your dApp Security?
Share this guide with your dev team. Bookmark it for reference. And if you're building something new, start with security from day one, not as an afterthought.
Got questions about smart contract audits or specific vulnerabilities? Consult now.
Share with your community!