Loading blog post...

9 Reasons You’re Not Reaching Full-Stack Security in Web3
Full-stack Web3 security isn’t about audits or checklists anymore—it’s about surviving in a fully adversarial ecosystem. In 2025, attackers exploit wallet UX, infrastructure, dependencies, governance, and community behavior just as aggressively as smart contracts. This guide breaks down the real reasons teams fail to achieve full-stack security and what it actually takes to build protocols that withstand modern Web3 threats.
Let’s stop pretending Web3 is a calm, decentralized sanctuary. It’s a hostile network where protocols survive only if their security posture evolves faster than the attackers studying them. In 2025, a protocol doesn’t lose because of “bad luck.” It loses because someone out there had more time, more automation, more motivation or more financial upside to break you.
Full-stack Web3 security isn’t a luxury anymore. It’s the bare minimum for any team that wants to avoid becoming another viral exploit thread. Attackers are not browsing your website, they’re scanning your bytecode, fingerprinting your frontend, probing your RPC provider and mapping your entire dependency chain long before your first user registers. If you’re wondering why full-stack security feels out of reach, here are the real reasons.
1. You Still Think a Web3 Security Audit Ends When the Report Arrives
The obsession with “getting audited” has become almost comical. A Web3 security audit is not an endpoint, and it never was. The moment you push a contract upgrade, integrate a new liquidity route, adjust an oracle source, or change a permission boundary, the previous audit becomes a historical artifact. Attackers don’t wait for your next engagement. They strike during migrations, feature launches, governance votes and dependency updates. The moments your team least expects it. If your security model freezes after the audit, your attack surface stays wide open.
For readers evaluating audit readiness, your technical team can explore our smart contract audit services.
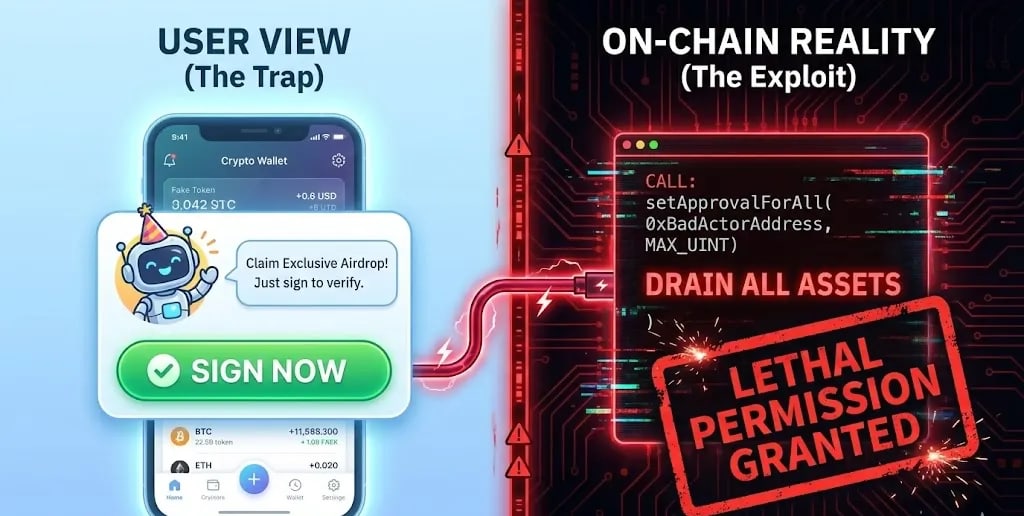
2. Your Web3 Wallet Experience Still Exposes Users to Signing Traps
Smart contracts get attention, but the Web3 wallet layer remains the easiest kill zone. Blind signing, confusing prompts, unrevoked approvals, unsafe transaction building, and unclear permission flows give attackers exactly what they want: a user who authorizes theft without realizing it. The irony is brutal, teams spend months perfecting Solidity, only to expose their users to drainers because they didn’t treat wallet UX as part of the security perimeter. You can’t claim full-stack protection if your wallet flow is the weakest link.
3. You Work With a Web3 Development Company That Builds Features but Not Security Foundations
Most agencies can deploy a dApp. Very few can architect one that stands up to adversarial pressure. A Web3 development company that prioritizes delivery speed over structural integrity creates ticking time bombs: upgrade logic that collapses in edge cases, permission systems without blast radius limits, automation scripts without signing safeguards, fallback functions that behave unpredictably under stress and storage layouts that break during future refactors. Attackers don’t exploit the code you wrote last night. they exploit the architecture mistakes made on day one.
If you want architecture built for real adversarial conditions, you can enquire with our Web3 development agency to audit your current foundation or architect your protocol from scratch with adversarial modeling in place.
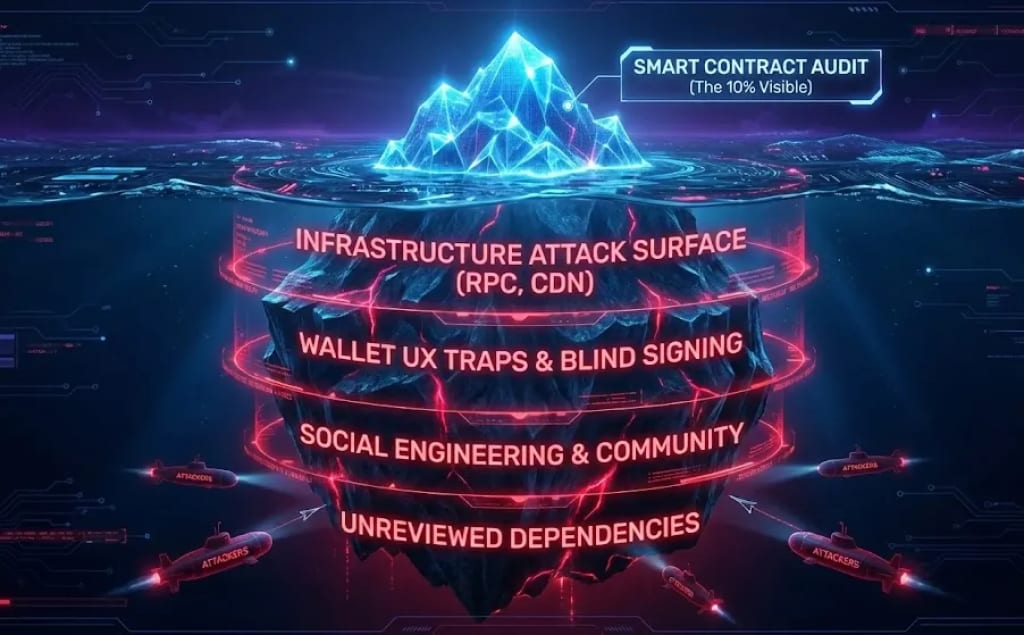
4. You Don’t Realize Your Infrastructure Is One Giant Attack Surface Waiting for a Weak Moment
Web3 is not “just smart contracts.” It’s RPC nodes, indexers, cloud functions, schedulers, CDNs, server-side scripts, monitoring agents, frontend deployments, and off-chain automations. Any single misconfiguration compromises the entire stack. A poisoned CDN can replace your UI with a malicious transaction builder. A compromised RPC provider can manipulate gas estimates or reorder user transactions. A single unprotected automation key can override thousands of contract interactions. Infrastructure security isn’t secondary, it’s the battleground attackers love the most.
5. Your Web3 Community Isn’t Trained for Social Engineering, and Attackers Know It
Security is never just technical. It’s behavioral and your Web3 community is part of your trust boundary whether you admit it or not. Attackers target Discord mods, Telegram admins, DAO voters, and the loudest community members. Impersonation traps, fake governance proposals, malicious bots, weaponized airdrops, and DM-based drainers all thrive in communities that haven’t been educated. One compromised moderator account can cause more damage than a smart contract bug. If your community is uninformed, your protocol becomes collateral.
If you want to build a community that’s resilient, informed, and impossible to manipulate, check out our Web3 social media management services, where education, narrative shaping, and real-time security awareness become part of your defense system.
6. You Don’t Follow the Real-Time Monitoring Standards of a Mature Web3 Development Agency
A professional Web3 development agency doesn’t treat deployment as the finish line, it treats it as the beginning of live combat. The protocols that survive monitor the mempool like predators. They track abnormal state transitions, suspect admin patterns, timing irregularities, MEV-adjacent execution, and transaction clusters that signal reconnaissance attempts. The teams that lose always have the same post-exploit statement: “We didn’t see it happening.” Of course they didn’t. They weren’t looking.
For teams building advanced monitoring pipelines, our custom dApp building service can be integrated directly into your workflow.
7. You Blindly Trust Open Source Dependencies Without Reviewing the Hidden Exploit Paths
Open source accelerates development, but it also imports vulnerabilities silently and at scale. A governance library can introduce unseen privilege escalation. A popular proxy pattern may contain subtle upgrade hazards. A math utility that everyone uses can hide edge-case overflow conditions. The worst attacks don’t come from your own code, they come from code you inherited because “everyone else uses it.” Security is not just what you write. It’s everything you integrate without questioning.
8. You Don’t Simulate the Black-Swan Conditions Attackers Actively Hunt For
Every catastrophic Web3 exploit in the past three years had one thing in common: the exploited scenario was dismissed as “unlikely” during development. Attackers weaponize the edges — desynchronized price feeds, untested token decimals, reorg-sensitive logic, timestamp drift, MEV timing windows, composability side effects, and flash-loan-amplified sequences. These aren’t theoretical attack paths. They’re profitable ones. If you aren’t simulating chaos, your assumptions are writing checks your protocol can’t cash.
9. You Deploy Without the Operational Discipline Required for High-Stakes Systems
Security isn’t defined by clean code or a green audit badge. It’s defined by resilience under stress, predictable behavior under uncertainty, and controlled access under every circumstance. A secure protocol uses time-delayed critical actions, multi-signature controls, fallback logic with circuit breakers, oracle validation with sanity checks, rate-limited sensitive operations, and monitoring systems that detect anomalies before users ever feel the impact. If your deployment process doesn’t reflect the reality of adversarial conditions, your protocol isn’t ready for public liquidity.
FAQ: Full-Stack Web3 Security
Q: Why isn’t a Web3 security audit enough anymore?
A: Because an audit is a snapshot, not a living defense system. Attackers strike during upgrades, governance changes, migrations, or dependency shifts moments that occur after the audit. Static reviews can’t protect a dynamic protocol.
Q: What’s the most common entry point attackers target now?
A: Not smart contracts, it’s frontend infrastructure and wallet signing flows. A poisoned CDN or a malicious signing prompt drains more users than a Solidity bug ever will.
Q: Do I really need to worry about my Web3 community for security?
A: Yes. Your community is part of your security perimeter. One compromised moderator or governance participant can cause more damage than a critical contract vulnerability.
Q: How do I know if my Web3 development company understands security or just ships features?
A: Feature-focused teams optimize for speed. Security-focused teams optimize for blast radius, upgrade safety, permission design, fallback logic, and adversarial behavior. If they don’t mention these, they’re not protecting you.
Q: What does “full-stack Web3 security” actually include?
A: Everything:
- smart contracts
- wallets
- RPC nodes
- indexers
- automation scripts
- governance
- frontend infrastructure
- community behavior
- monitoring pipelines
A protocol is only as secure as its weakest surface.
Q: Is real-time monitoring really that important?
A: Yes. Most major exploits were detectable minutes sometimes hours before the actual attack. Teams who monitor the mempool, admin patterns, and execution anomalies catch what everyone else misses.
Q: Should I avoid open-source dependencies?
A: No, but you must review them like they were your own attack surface. The most damaging exploits often come from blindly imported libraries buried deep in your stack.
Q: How do I prepare for a future audit the right way?
A: Clean architecture, clear permission boundaries, documented assumptions, stable upgrade plans, and pre-audit internal testing. If you’re preparing for a formal assessment, you can check out our smart contract audit services for Web3 applications.
The Bottom Line: Full-Stack Security Isn’t a Tagline, It’s Survival
Smart contracts are only one slice of the danger. Wallets, infrastructure, governance, automation, nodes, and community all carry their own attack surfaces. Protocols don’t fail because attackers are unstoppable. They fail because teams underestimate how sophisticated the ecosystem has become.
Fix these nine foundational issues and you’re no longer hoping your protocol survives, you’re engineering its survival.
Share with your community!